
Wednesday, February 6, 2008
Tuesday, February 5, 2008
Monday, January 28, 2008
DATACOM
Network Evolution
Continuously evolving for more than 30 years
Provides companies with the ability to share data between systems
Database
Web
History
Required “sneakernet” to share data
Host computing (centralized)
Mainframe from single vendor
User terminals were not intelligent
Relied on centralized host for all capabilities
IBM, Digital, etc.
Types
Local Area Networks (LAN)
PC-based
Sometimes known as Intranet
Used within a single facility (campus) to share data between PC systems
Novell Netware, Microsoft Windows networking
Metropolitan Area Networks (MAN)
Several LAN that cover a larger area or connect a few campus networks together
Usually within the same city and use a short-range connectivity solutions
Microware or laser
Wide Area Network (WAN)
Network spread over a very large geographical area
Uses technologies which allow longer distance to be obtained
Phone service or satellite
Enterprise
Extranet or Virtual Private Network (VPN)
Utilizes public medium, such as the Internet, to connect external devices to an Intranet
VPN – Remote access employees
Extranet – Partner or affiliate companies
Storage Are Network (SAN)
Supports disk mirroring, backup and restore, archival and retrieval of archived data, data igration, and sharing of data among different network servers in a network
Content Delivery Network
Service of copying pages of Web site to geographically disperse servers
Dynamically identifies and serves page content from the closest server to the user, enabling faster delivery
Typically, high-traffic website owners and Internet Service Providers (ISPs) hire services of companies that provide content delivery
Internetworking
The process of interconnecting two or more individual networks to facilitate communications among their respective parts
may be of different types, each having its address, internal protocols, access methods, and administration
The focus is the ability to communicate dissimilar media types
No one solution right for everyone
Must provide
Reliable communication
Scalability / expandability
Manageability
Security
TCP/IP Connectivity
In 1969 – Department of Defense commissioned Advanced Research Projects Agency (ARPA) networks
ARPANET used Network Connection Protocol (NCP)
TCP/IP research began
Stanford University
Funding by Department of Defense
Developed a four layer networking model
Research published in Request for Comments (RFCs)
Internetworking, as we know it, was born
De facto standard
OSI Model
1970 – International Organization of Standardization (ISO) began work seven-layer model
Open Systems Interconnection (OSI) was born
Created a full standard set for all internetworking communications
1979 OSI completed
Creation of the Distribution Processing model
LAN and WAN definitions were born
Ethernet
1970s – Digital, Intel, and Xerox (DIX) consortium created the original Ethernet
Ethernet II standard was subsequently defined and released
Known as ARPA Ethernet
802.x
1980 – Institute of Electrical and Electronic Engineers, Inc. (IEEE) to on Project 802
802.2 – Logical Link Control (LLC) focus on end-to-end link connectivity and the interface between the higher layers and the medium-access-dependent layers
802.3 – Became the Ethernet standard (pushed by DIX)
802.4 – Token Bus
802.5 – Token Ring (pushed by IBM)
Requirements for Network connection
Physical connection
Logical connection
protocols
Applications
interpret the data and display the information
How network send data?
Packets are basic units for network communication
Send the original, disassembled data in small chunks.
Reassemble the data in the proper order when it reaches its destination.
Check the data for errors after it has been reassembled.
Network Devices
Equipments that connect directly to a network segment
Two Classifications of Network Devices
End-User devices
Network devices
Friday, January 25, 2008
DATACOM(assignment)

A local area network (LAN) is a group of computers and associated devices that share a common communications line or wireless link. Typically, connected devices share the resources of a single processor or server within a small geographic area (for example, within an office building). Usually, the server has applications and data storage that are shared in common by multiple computer users. A local area network may serve as few as two or three users (for example, in a home network) or as many as thousands of users (for example, in an FDDI network).
What is WAN?

A wide area network (WAN) is a geographically dispersed telecommunications network. The term distinguishes a broader telecommunication structure from a local area network (LAN). A wide area network may be privately owned or rented, but the term usually connotes the inclusion of public (shared user) networks. An intermediate form of network in terms of geography is a metropolitan area network (MAN).
What is MAN?
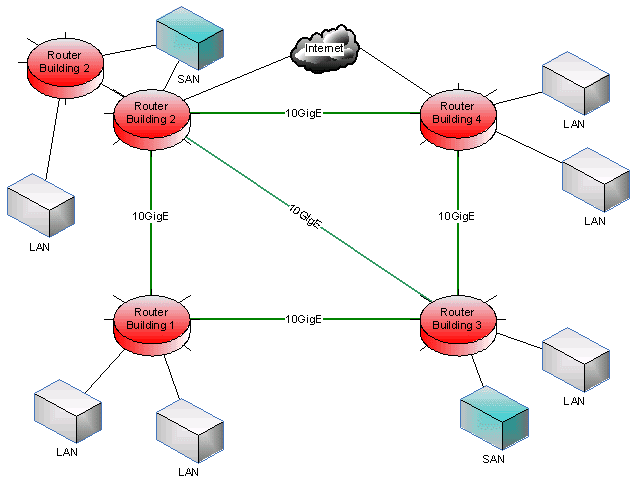
A metropolitan area network (MAN) is a network that interconnects users with computer resources in a geographic area or region larger than that covered by even a large local area network (LAN) but smaller than the area covered by a wide area network (WAN). The term is applied to the interconnection of networks in a city into a single larger network (which may then also offer efficient connection to a wide area network). It is also used to mean the interconnection of several local area networks by bridging them with backbone lines. The latter usage is also sometimes referred to as a campus network.
What is SAN?

A storage area network (SAN) is a high-speed special-purpose network (or subnetwork) that interconnects different kinds of data storage devices with associated data servers on behalf of a larger network of users. Typically, a storage area network is part of the overall network of computing resources for an enterprise. A storage area network is usually clustered in close proximity to other computing resources such as IBM z990 mainframes but may also extend to remote locations for backup and archival storage, using wide area network carrier technologies such as ATM or SONET.
Small Area Networks typically include one or more master devices that communicate with one or more slave devices using a serial (one bit at a time) protocol over a common wire bus that connects all the devices together. A master can get the attention of a slave device by sending the slave address over the common wire bus, or by applying a signal to separate device select lines.
There are a wide variety of Small Area Networks in use today. These include Inter-Intergrated Circuit Bus (I2C Bus), System Management Bus (SMBus), Serial Peripheral Interface (SPI), 1-Wire, and more. Each bus type offers characteristics such as cost and flexibility that can make it better suited to specific applications
What is DATA CENTERS?

A data center (sometimes spelled datacenter) is a centralized repository, either physical or virtual, for the storage, management, and dissemination of data and information organized around a particular body of knowledge or pertaining to a particular business. The National Climatic Data Center (NCDC), for example, is a public data center that maintains the world's largest archive of weather information. A private data center may exist within an organization's facilities or may be maintained as a specialized facility. According to Carrie Higbie, of Global Network Applications, every organization has a data center, although it might be referred to as a server room or even a computer closet. In that sense, data center may be synonymous with network operations center (NOC), a restricted access area containing automated systems that constantly monitor server activity, Web traffic, and network performance.
What is Intranet?

An intranet is a private network that is contained within an enterprise. It may consist of many interlinked local area networks and also use leased lines in the wide area network. Typically, an intranet includes connections through one or more gateway computers to the outside Internet. The main purpose of an intranet is to share company information and computing resources among employees. An intranet can also be used to facilitate working in groups and for teleconferences.
An intranet uses TCP/IP, HTTP, and other Internet protocols and in general looks like a private version of the Internet. With tunneling, companies can send private messages through the public network, using the public network with special encryption/decryption and other security safeguards to connect one part of their intranet to another.
Typically, larger enterprises allow users within their intranet to access the public Internet through firewall servers that have the ability to screen messages in both directions so that company security is maintained. When part of an intranet is made accessible to customers, partners, suppliers, or others outside the company, that part becomes part of an extranet.
What is VPN (Virtual Private Networking)?

VPN gives extremely secure connections between private networks linked through the Internet. It allows remote computers to act as though they were on the same secure, local network.
Advantages
Allows you to be at home and access your company's computers in the same way as if you were sitting at work.
Almost impossible for someone to tap or interfer with data in the VPN tunnel.
f you have VPN client software on a laptop, you can connect to your company from anywhere in the world.
Disadvantages
Setup is more complicated than less secure methods. VPN works across different manufacturers' equipment, but connecting to a non-NETGEAR product will add to difficulty, since there may not documentation specific to your situation.
The company whose network you connect to may require you to follow the company's own policies on your home computers ( ! )
VPN goes between a computer and a network (client-to-server), or a LAN and a network using two routers (server-to-server). Each end of the connection is an VPN "endpoint", the connection between them is a "VPN tunnel". When one end is a client, it means that computer is running VPN client software such as NETGEAR's ProSafe VPN Client. The two types of VPN:
Thursday, January 24, 2008
DATACOM
Connecting to the Internet
Internet is a valuable resource, and connecting to it is essential for business and industry and education. Building a network that will connect to the internet requires CAREFUL PLANNING. Computer as well as the device itself must be considered. The correct protocol must be configured.
Requirement for internet connection
The internet is the largest data network in the world. The internet is consist of millions of interconnected networks.
Logical Connection – logical connection uses standard protocol connecting to the internet uses multiple protocol. The Transmission Control Protocol / Internet Protocol or TCP/IP suite is the primary protocol used on the internet
Applications – it interprets the data and displays information in an understandable format. Application.
Backplane components of your computer Mboard,Memory,VideoCard,Parallel ports,
serial ports.
Browsers and Plug-ins
IE
Takes up more disk space
Display HTML perform email.
Communicator
Takes up less disk space
Display HTML perform email.
Bit - Smallest unit of data in a computer 8 bits = 1 byte
Byte - A unit of measure that describes the size of a data file, the amount of space on a disk or another storage medium, or the amount of data being transferred over a network.
Kbps - A standard measurement of the rate at which data is transferred over a network connection.
MHz - A unit of frequency; the rate of change in the state or cycle in a sound wave alternating current
Network Math
Binary – Number system that is characterized by 1’s and 0’s. In computer Bits are binary Digits that are represented by on/off or the presence or absence of electrical charges.
Hexadecimal – another number system that uses 16 symbols because only tem symbols represent digits (0 – 9)and because base16 requires more 6 symbols the extra symbols are the letters A,B,C,D,E and F.
A = 10 , B=11, C=12, D=13, E=14, F=15,
the position of each symbols (digits) in a hex number represents the base number 16 raise to a power base on its position. Moving from right to left our network adopter or NIC addresses are expressed as a string of 12 hexadecimal characters.
4 Octet Dotted-Decimal representation of a 32-bit Binary Number
When written the complete decimal number is represented as four groups of decimal digits separated by periods. Such as 10.15.129.201 this is a sample of an IP address . this is called dotted-decimal notation and provides a compact, easy-to-remember way of referring to 32-bit addresses.
10 = 00001010
15 = 00001111
129 = 10000001
201= 11001001
For Ethernet this MAC addresses are 48bit or six octets. Because this address is consist of six distinct octets. They can be expressed as 12 hex numbers instead. Every 4 bits is a hex digits
Example :
10101010.11110000.11000001.11100010.01110111.01010001
Mac Address
AA.F0.C1.E2.77.51
A = 1010, A = 1010, F = 1111, 0 = 0000, C = 1100, 1 = 0001, E = 1110,
2 = 0010, 7 = 0111, 7 = 0111, 5 = 0101, 1 = 0001
IP address
The 32 bit binary addresses used on the internet are called Internet Protocol addresses.
1.) 32-bit address assigned to hosts using TCP/IP. An IP address belongs to one of five classes (A, B, C, D, or E) and is written as 4 octets separated with periods (dotted decimal format). Each address consists of a network number, an optional subnetwork number, and a host number. A subnet mask is used to extract network and subnetwork information from the IP address. Also called an Internet address.
2.) Command used to establish the logical network address of this interface.
IP address
Testing Connectivity with Ping Command
Ping is a program that is useful for verifying a successful TCP/IP installation. It is named after the sonar Operation used to locate and determine the distance to an underwater object. PING stands for Packet INTERNETWORK GROUPER
Ping command works by sending internet Control Message Protocol (ICMP) datagram's to request a reply. The output response for a ping contains the success ratio and round-trip time to the destination.
Ping command also use to test NIC transmit/ receive function, TCP/IP configuration, and Network connectivity.
IP address
Usage of PING Command
127.0.0.1 (Internal Loopback test) – because no packets are transmitted pinging the loop back interface tests basic TCP/IP network configuration.
Ping IP address of the host computer – Verifies the TCP/IUP address configuration for the local host.
Ping the default gateway IP address – verifies whether the router that connects the local network to other networks can be accessed.
Ping Remote Destination host – Ping www.yahoo.com / ping www.google.com.
DATACOM
(Advance Research Program Networking)

The precursor to the Internet, ARPANET was a large wide-area network created by the United States Defense Advanced Research Project Agency (ARPA). Established in 1969, ARPANET served as a testbed for new networking technologies, linking many universities and research centers. The first two nodes that formed the ARPANET were UCLA and the Stanford Research Institute, followed shortly thereafter by the University of Utah.
What is IEEE?
(Institute of Electrical and Electronics Engineers)

A non-profit organization, IEEE is the world's leading professional association for the advancement of technology.
The IEEE name was originally an acronym for the Institute of Electrical and Electronics Engineers, Inc. Today, the organization's scope of interest has expanded into so many related fields, that it is simply referred to by the letters I-E-E-E (pronounced Eye-triple-E).
What is OSI?
(Open System Interconnection)
 Open System Interconnection, an ISO standard for worldwide communications that defines a networking framework for implementing protocols in seven layers. Control is passed from one layer to the next, starting at the application layer in one station, proceeding to the bottom layer, over the channel to the next station and back up the hierarchy.
Open System Interconnection, an ISO standard for worldwide communications that defines a networking framework for implementing protocols in seven layers. Control is passed from one layer to the next, starting at the application layer in one station, proceeding to the bottom layer, over the channel to the next station and back up the hierarchy.At one time, most vendors agreed to support OSI in one form or another, but OSI was too loosely defined and proprietary standards were too entrenched. Except for the OSI-compliant X.400 and X.500 e-mail and directory standards, which are widely used, what was once thought to become the universal communications standard now serves as the teaching model for all other protocols.
Most of the functionality in the OSI model exists in all communications systems, although two or three OSI layers may be incorporated into one.
The 7 Layers of the OSI Model

7. application
4. transport
Examples of upper layer technologies in the OSI model are HTTP, SSL and NFS.
Application(Layer 7)
This layer supports application and end-user processes. Communication partners are identified, quality of service is identified, user authentication and privacy are considered, and any constraints on data syntax are identified. Everything at this layer is application-specific. This layer provides application services for file transfers, e-mail, and other network software services. Telnet and FTP are applications that exist entirely in the application level. Tiered application architectures are part of this layer.
This layer provides independence from differences in data representation (e.g., encryption) by translating from application to network format, and vice versa. The presentation layer works to transform data into the form that the application layer can accept. This layer formats and encrypts data to be sent across a network, providing freedom from compatibility problems. It is sometimes called the syntax layer.
This layer establishes, manages and terminates connections between applications. The session layer sets up, coordinates, and terminates conversations, exchanges, and dialogues between the applications at each end. It deals with session and connection coordination.
This layer provides transparent transfer of data between end systems, or hosts, and is responsible for end-to-end error recovery and flow control. It ensures complete data transfer.
This layer provides switching and routing technologies, creating logical paths, known as virtual circuits, for transmitting data from node to node. Routing and forwarding are functions of this layer, as well as addressing, internetworking, error handling, congestion control and packet sequencing.
At this layer, data packets are encoded and decoded into bits. It furnishes transmission protocol knowledge and management and handles errors in the physical layer, flow control and frame synchronization. The data link layer is divided into two sublayers: The Media Access Control (MAC) layer and the Logical Link Control (LLC) layer. The MAC sublayer controls how a computer on the network gains access to the data and permission to transmit it. The LLC layer controls frame synchronization, flow control and error checking.
This layer conveys the bit stream - electrical impulse, light or radio signal -- through the network at the electrical and mechanical level. It provides the hardware means of sending and receiving data on a carrier, including defining cables, cards and physical aspects. Fast Ethernet, RS232, and ATM are protocols with physical layer components.

